UEFI scanning in Defender for Endpoint
Recently, Microsoft Defender for Endpoint extended its protection capabilities to the firmware level with a new Unified Extensible Firmware Interface (UEFI) scanner.
Hardware and firmware-level attacks have continued to rise in recent years, as modern security solutions made persistence and detection evasion on the operating system more difficult. Attackers compromise the boot flow to achieve low-level malware behavior that's hard to detect, posing a significant risk to an organization's security posture.
Windows Defender System Guard helps defend against firmware attacks by providing guarantees for secure boot through hardware-backed security features like hypervisor-level attestation and Secure Launch, also known as Dynamic Root of Trust (DRTM), which are enabled by default in Secured-core PCs. The new UEFI scan engine in Defender for Endpoint expands on these protections by making firmware scanning broadly available.
The UEFI scanner is a new component of the built-in antivirus solution on Windows 10 and newer versions, and gives Defender for Endpoint the unique ability to scan inside of the firmware filesystem and perform security assessment. It integrates insights from our partner chipset manufacturers and further expands the comprehensive endpoint protection provided by Defender for Endpoint.
Prerequisites
- Microsoft Defender Antivirus as the primary antivirus product and in active mode. UEFI scanner doesn't work with EDR in block mode (with Microsoft Defender Antivirus in passive mode).
- Real-time protection is turned on
- Behavior monitoring is turned on
- Devices are running a current Microsoft Defender Antivirus platform version
- Devices are running one of the following versions of Windows:
- Windows 10, Windows 11 or newer on client devices
- Windows Server 2019, Windows Server 2022, or newer versions
- Windows Server 2012 R2 and Windows Server 2016 with the unified Defender for Endpoint client installed
What is the UEFI scanner?
The Unified Extensible Firmware Interface (UEFI) is a replacement for legacy BIOS. If the chipset is configured correctly (UEFI & chipset configuration itself) and secure boot is enabled, the firmware is reasonably secure. To perform a hardware-based attack, attackers exploit a vulnerable firmware or a misconfigured machine to deploy a rootkit, which allows attackers to gain foothold on the machine.
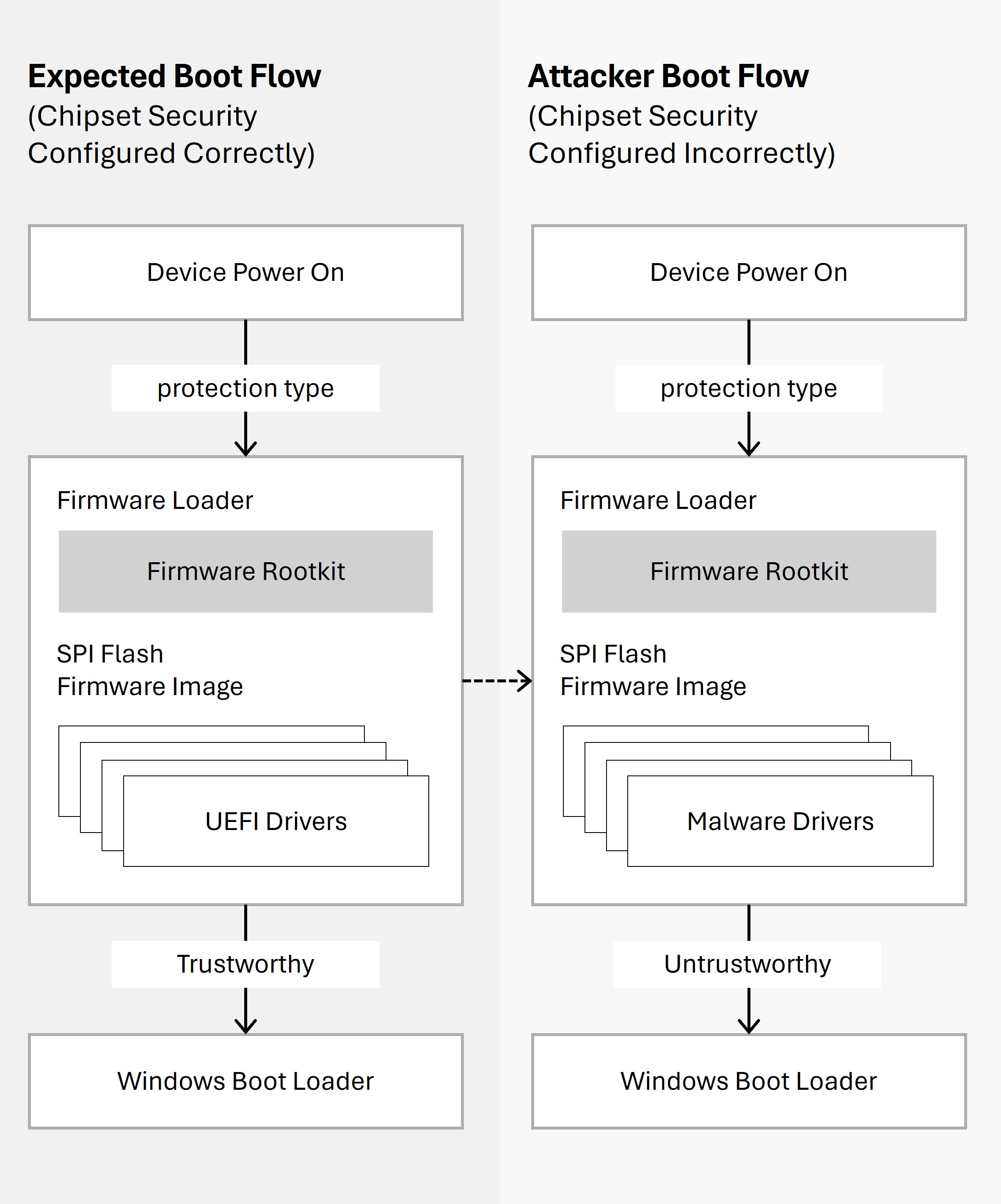
As the figure shows, for devices that are configured correctly, the boot path from power-on to OS initialization is reliable. If secure boot is disabled or if the motherboard chipset is misconfigured, attackers can change the contents of UEFI drivers that are unsigned or tampered with in the firmware. This could allow attackers to take over control of devices and give them the capability to deprivilege the operating system kernel or antivirus to reconfigure the security of the firmware.
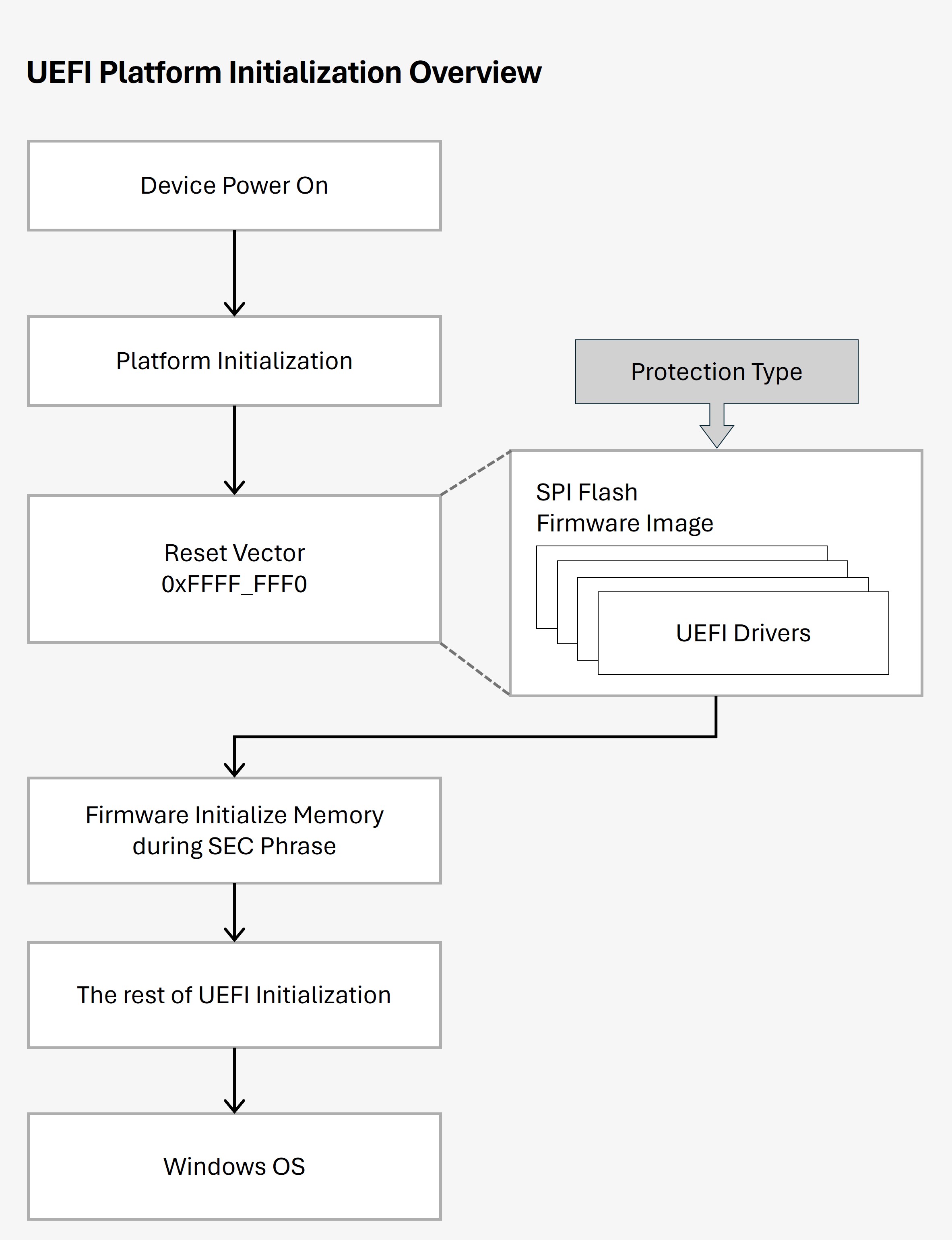
The Serial Peripheral Interface (SPI) flash stores important information. Its structure depends on OEM's design, and commonly includes processor microcode update, Intel Management Engine (ME), and boot image, a UEFI executable. When a computer runs, processors execute the firmware code from SPI flash for a while during UEFI's SEC phase. Instead of memory, the flash is permanently mapped to x86 reset vector (physical address 0xFFFF_FFF0). However, attackers can interfere with memory access to reset vector by software. They do this by reprogramming the BIOS control register on misconfigured devices, making it even harder for security software to determine exactly what gets executed during boot.
Once an implant is deployed, it's hard to detect. To catch threats at this level, security solutions at the OS level rely on information from the firmware, but the chain of trust is weakened.
Technically, the firmware isn't stored and isn't accessible from main memory. As opposed to other software, it's stored in SPI flash storage, so the new UEFI scanner must follow the hardware protocol provided by hardware manufacturers. To be compatible and be up to date with all platforms, it needs to take into consideration protocol differences.
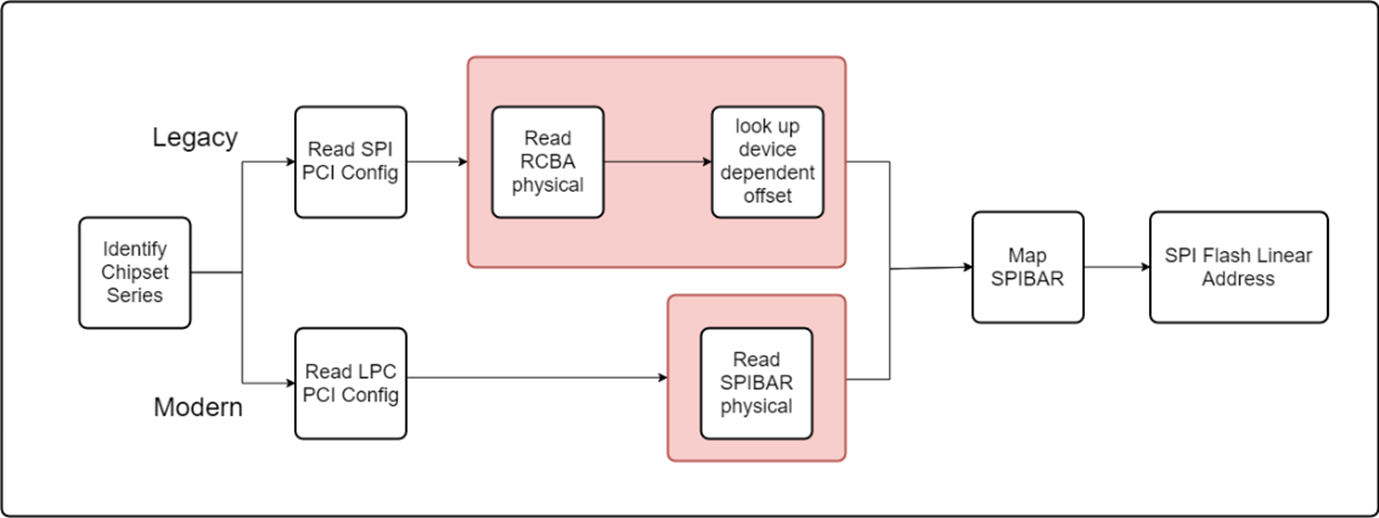
The UEFI scanner performs dynamic analysis on the firmware it gets from the hardware flash storage. By obtaining the firmware, the scanner is able to parse the firmware, enabling Defender for Endpoint to inspect firmware content at runtime.
How do you turn on the UEFI scanner?
The new UEFI scanner is a component of Microsoft Defender Antivirus, thus, as long as it's the primary AV, it includes this capability to scan and access UEFI firmware.
How do you manage the UEFI scanner?
It's a built-in functionality of Microsoft Defender Antivirus. Thus, there is no additional management.
How does the UEFI scanner in Defender for Endpoint work?
The new UEFI scanner reads the firmware file system at runtime by interacting with the motherboard chipset. To detect threats, it performs dynamic analysis using multiple new solution components that include:
- UEFI anti-rootkit, which reaches the firmware through Serial Peripheral Interface (SPI)
- Full filesystem scanner, which analyzes content inside the firmware
- Detection engine, which identifies exploits and malicious behaviors
Firmware scanning is orchestrated by runtime events like suspicious driver load and through periodic system scans. Detections are reported in Windows Security, under Protection history.
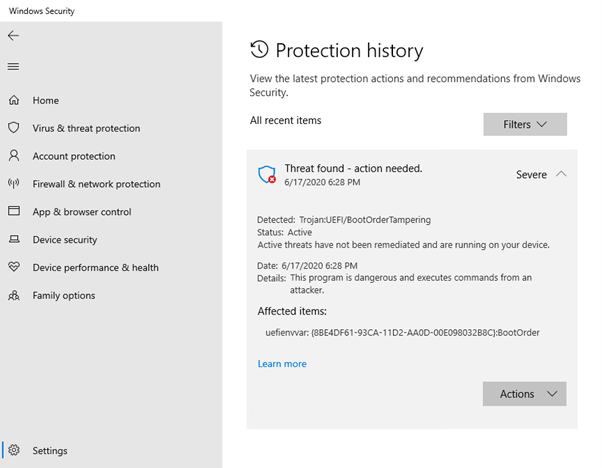
Defender for Endpoint customers can see these detections raised as alerts in the Microsoft Defender portal, empowering security operations teams to investigate and respond to firmware attacks and suspicious activities at the firmware level in their environments.
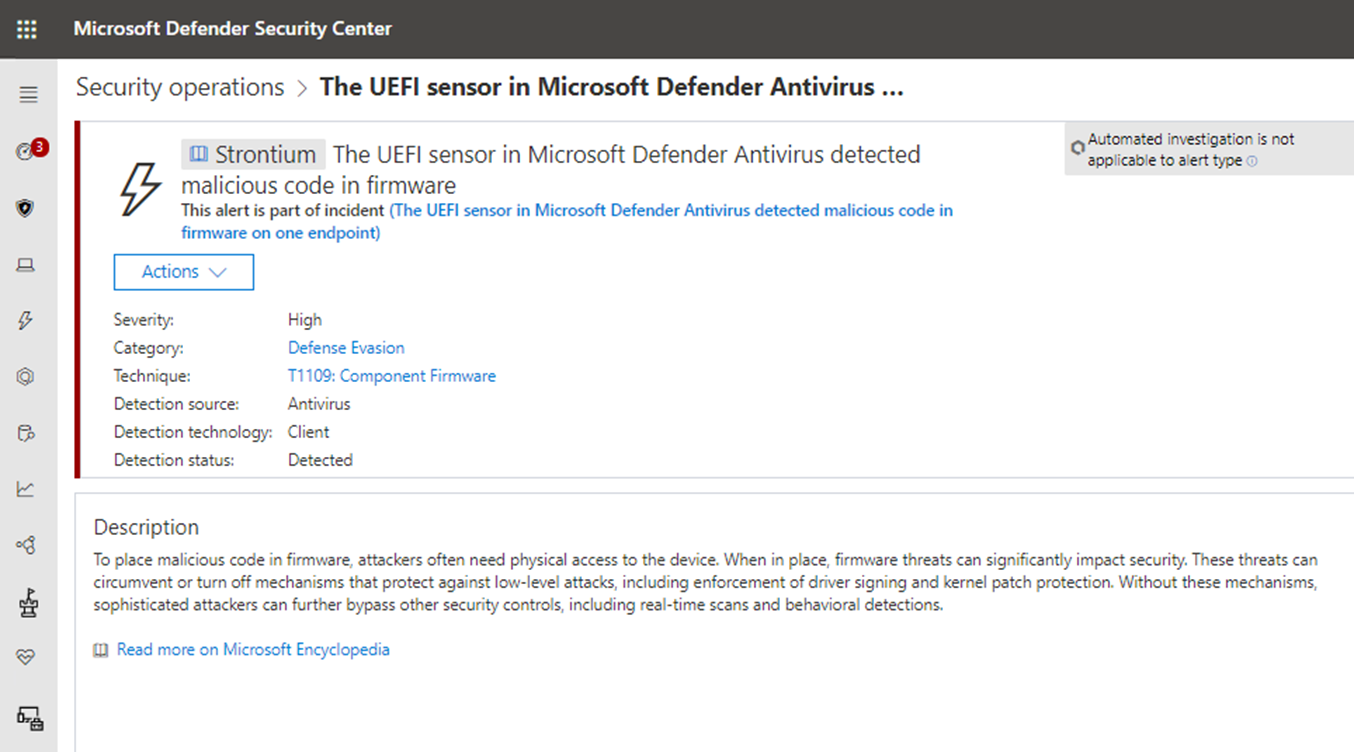
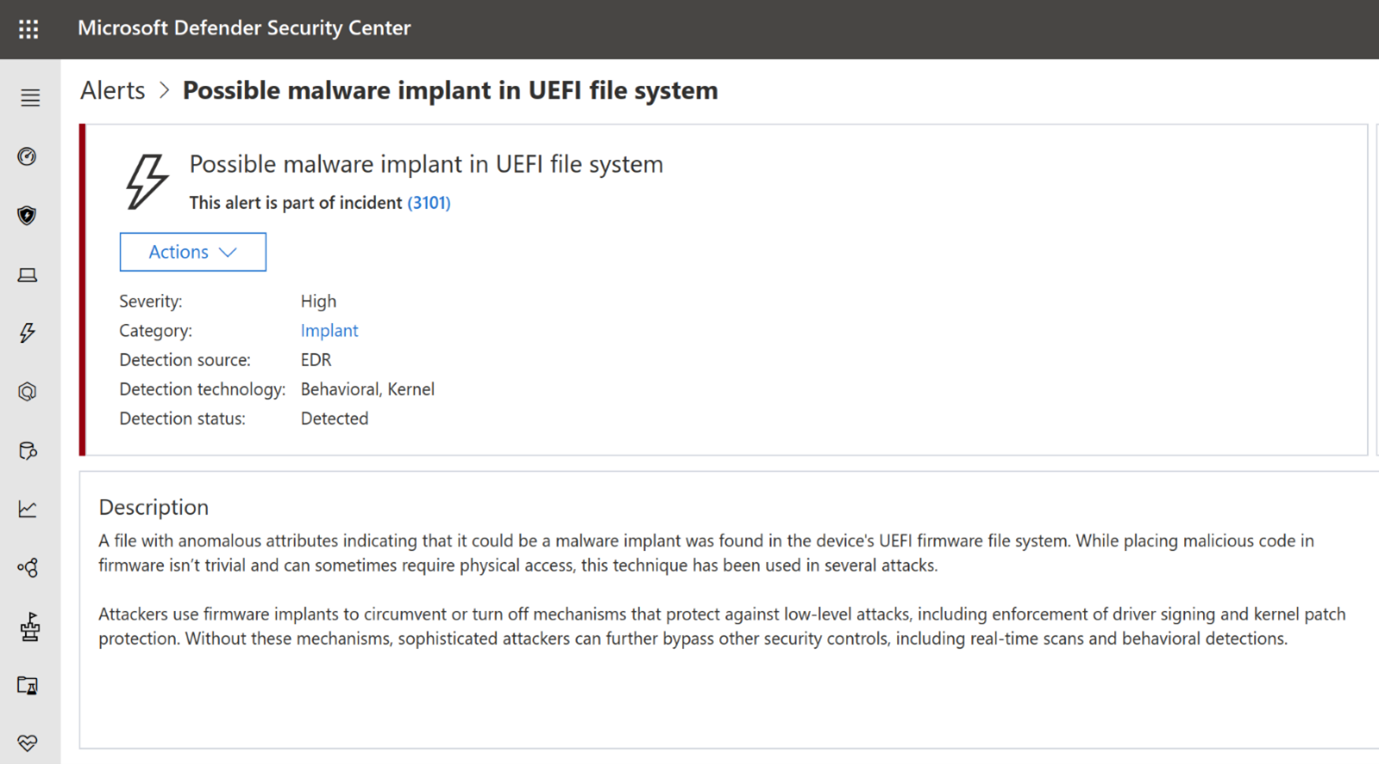
To detect unknown threats in SPI flash, signals from the UEFI scanner are analyzed to identify anomalies and where they have been executed. Anomalies are reported to the Microsoft Defender portal for investigation.
These events can likewise be queried through advanced hunting as shown:
DeviceAlertEvents
| where Title has "UEFI"
| summarize Titles=makeset(Title) by DeviceName, DeviceId, bin(Timestamp, 1d)
| limit 100
Comprehensive security levels up with low-level protections
The new UEFI scanner adds to a rich set of Microsoft technologies that integrate to deliver chip-to-cloud security, from a strong hardware root of trust to cloud-powered security solutions at the OS level.
Hardware backed security features like Secure Launch and device attestation help stop firmware attacks. These features, which are enabled by default in Secured-core PCs, seamlessly integrate with Defender for Endpoint to provide comprehensive endpoint protection.
With its UEFI scanner, Defender for Endpoint gets even richer visibility into threats at the firmware level, where attackers have been increasingly focusing their efforts on. Security operations teams can use this new level of visibility, along with the rich set of detection and response capabilities in Defender for Endpoint, to investigate and contain such advanced attacks.
This level of visibility is also available in the Microsoft Defender portal, which delivers an even broader cross-domain defense that coordinates protection across endpoints, identities, email, and apps.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for